Where did it all begin?
Tim Berners developed the www. World wide web is basically a project that stores the documents that are accessible across the world through the Internet.
Let me show you the world's first website😶🌫️

"Link to the world's first website" This website has a collection of resources about the Internet, Servers, Web model, etc.
Client-Server architecture
Suppose you want to access google.com from your browser(Client), by entering the domain name and clicking enter, The request is sent to the Google server, and it sends back the response to your browser.
These are the things happening when you inspect the web page, in a network domain. Large Data is transferred over the internet in the form of packets or small chunks of data.
Data transfer through IP (Internet Protocol) address involves sending these packets of data from one device to another using their IP addresses. An IP address is a unique identifier assigned to every device that is connected to a network, whether it is a local network or the internet.
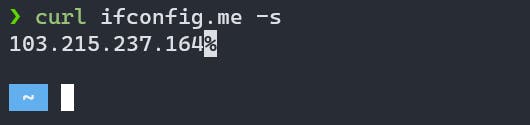
Command to know your IP Address:
curl ifconfig.me -s
How does your machine get an IP Address?
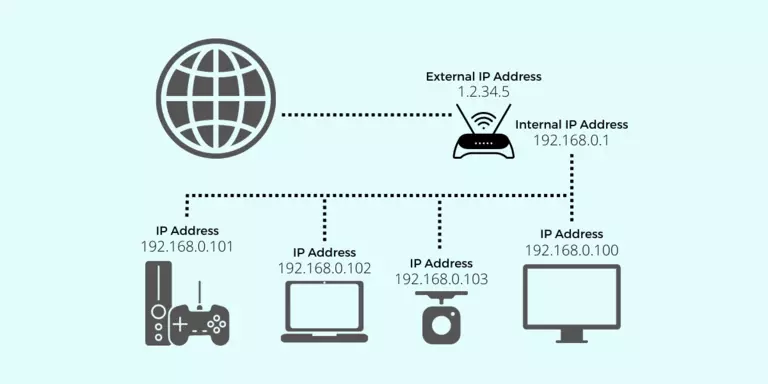
You buy a Modem/Router from the Internet Service Provider(ISP) to access the Internet, which contains a global IP Address. All the devices connected to this router will have the same IP address. And the router will assign each device a local IP address. It is done based on DHCP(Dynamic Host Configuration Protocol). When any of these devices makes a request to any server on the internet, that site for example let's say google.com can see the Global IP address.
The response sent by google.com comes to the router and is then sent to the device that actually requested through NAT(Network Access Translator). And in that particular device there might be many applications accessing the internet, so to which application the response should be transferred is decided upon port numbers.
There are 216 ports available in total, and ports from 0 to 1023 are reserved. These are the ports which are typically associated with specific protocols or services, they are not limited to those uses. Applications and services can use any available port, including reserved ports, as long as they do not conflict with other applications or services on the same device.
Some of the most commonly used reserved ports include:
Port 80: This is the port used by HTTP (Hypertext Transfer Protocol) for web traffic.
Port 443: This is the port used by HTTPS (HTTP Secure) for secure web traffic.
Port 22: This is the port used by SSH (Secure Shell) for secure remote access.
Ports from 1024 to 49151 are called registered ports that are assigned by the Internet Assigned Numbers Authority (IANA) to certain services or applications.
Port 3306: This is the port used by MySQL
Port 27017: This is the port used by MongoDB
The port range from 49152 to 65535 is known as the dynamic or private port range which is available for your own use to run your applications.
What are Network Protocols
What are the essential requirements to Communicate?
A common language for both ends to understand
A way to address to whom you want to communicate
A connection for the content to reach the recipient.
Think of any example you are a part of in your daily routine such as sending an E-mail, phone calls, or even video calls. All these require the before stated points.
And the rules for these steps to take place in a defined order are called "Protocols".
Some of the most commonly used protocols are:
TCP (Transmission Control Protocol): A protocol that provides reliable, ordered, and error-checked delivery of data packets over a network.
IP (Internet Protocol): A protocol responsible for addressing and routing data packets across networks, enabling communication between devices.
FTP (File Transfer Protocol): A protocol used for transferring files between a client and a server over a network.
HTTP (Hypertext Transfer Protocol): A protocol used for transmitting web pages and other data on the World Wide Web.
HTTPS (Hypertext Transfer Protocol Secure): A secure version of HTTP that encrypts data transmission to ensure secure communication.
SMTP (Simple Mail Transfer Protocol): A protocol used for sending email messages between servers.
IMAP (Internet Message Access Protocol): A protocol used by email clients to retrieve emails from a mail server.
POP (Post Office Protocol): A protocol used for downloading email messages from a mail server to a client device.
DNS (Domain Name System): A protocol that translates domain names (like example.com) into IP addresses, enabling easy access to websites and services on the internet.
Network Devices
Network devices are hardware components that are used to connect devices and enable communication between them.
Some of the most common network devices include:
Routers: These are devices that are used to connect multiple networks together and route data between them based on IP addresses.
:max_bytes(150000):strip_icc()/71qNsDlUZL._SL1500_-db9624bf30494933b4d2279b89ea19ef.jpg)
Switches: These are devices that are used to connect devices within a network and facilitate communication between them.

- Hubs: These are devices that are used to connect multiple devices within a network and broadcast data to all devices connected to the hub.
Repeaters: These are devices that are used to amplify and regenerate network signals over long distances.

Gateways: These are devices that are used to connect different types of networks together, such as a local area network (LAN) and a wide area network (WAN).

Geographic scope and scale of the network.
LAN (Local Area Network) is a type of network that connects devices within a small geographic area, such as a home, office, or school. Devices on a LAN can communicate with each other directly, without the need for an internet connection. Examples of devices that can be connected to a LAN include computers, printers, and routers.
WAN (Wide Area Network) is a type of network that connects devices across a large geographic area, such as across cities, countries, or even continents. WANs typically use the internet or other telecommunications networks to connect devices.
SONET (Synchronous Optical Network) and Frame Relay are two technologies commonly used in Wide Area Networks (WANs) to transport data over long distances.
SONET is a fiber optic communication system that provides high-speed data transmission rates of up to 10 Gbps. It uses synchronous transmission technology and is particularly suited for long-haul transmission over large distances.
Frame Relay is a WAN protocol that operates at the data link layer of the OSI model. It uses virtual circuits to establish logical connections between devices, allowing data to be transmitted efficiently over shared resources.
Examples of devices that can be connected to a WAN include servers, routers, and modems.
- MAN (Metropolitan Area Network) is a type of network that connects devices within a larger geographic area than a LAN, but smaller than a WAN. A MAN typically covers a geographic area the size of a city or town. MANs are typically used by businesses, universities, or other organizations that need to connect multiple locations within a city or town. Examples of devices that can be connected to a MAN include switches, routers, and hubs.
In summary, LANs connect devices within a small geographic area, WANs connect devices across large geographic areas, and MANs connect devices within a larger geographic area than a LAN but smaller than a WAN.
Network Topology

Network topology refers to the physical or logical layout of a network, let's see a few types of them:
Bus Topology: There is a Backbone network and computers are connected to it. If the link gets broken, the entire network is spoiled. Only one device can send data at a time because of this single network channel.
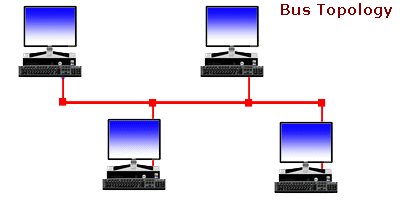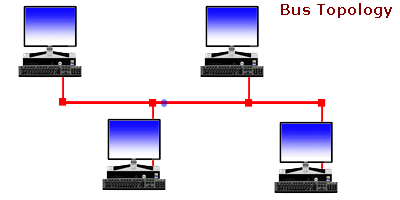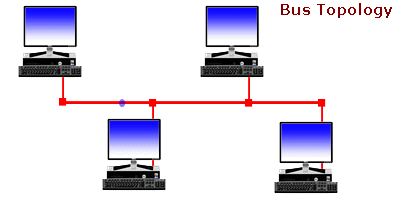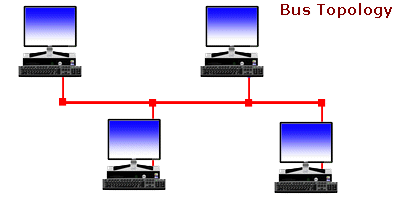
Ring Topology: Computers are connected in a ring-like structure. The connection between each device in this network enables ease of communication. The limitations are unwanted calls being received by the devices that are in between the 2 devices that want to communicate, and if the link breaks the network is lost.
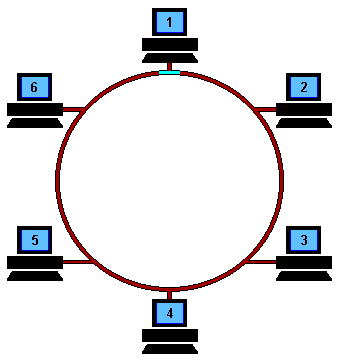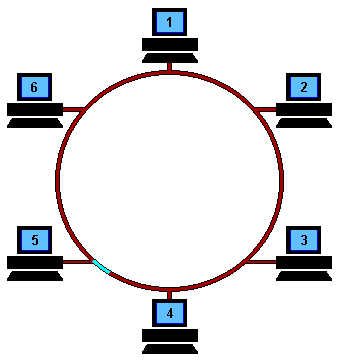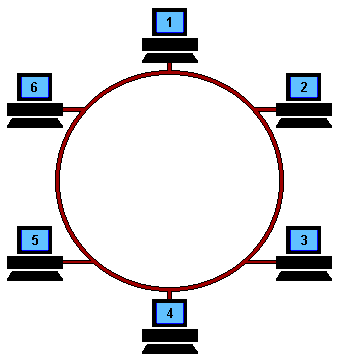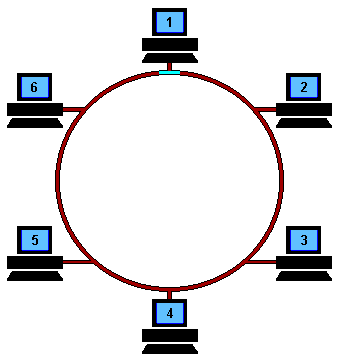
Star Topology: There is one central device that is connected to all the devices in the network. Make sure that the central device is stable and running all the time or else the network is collapsed.
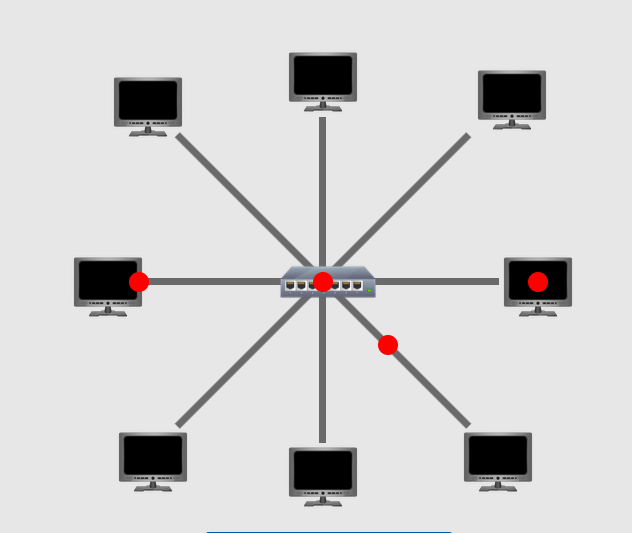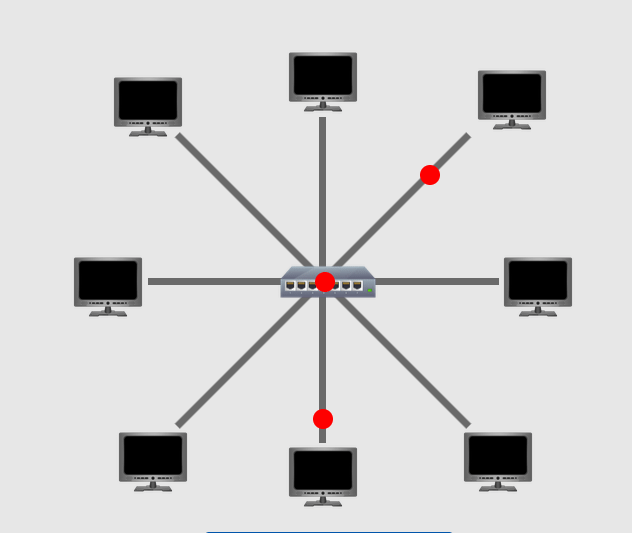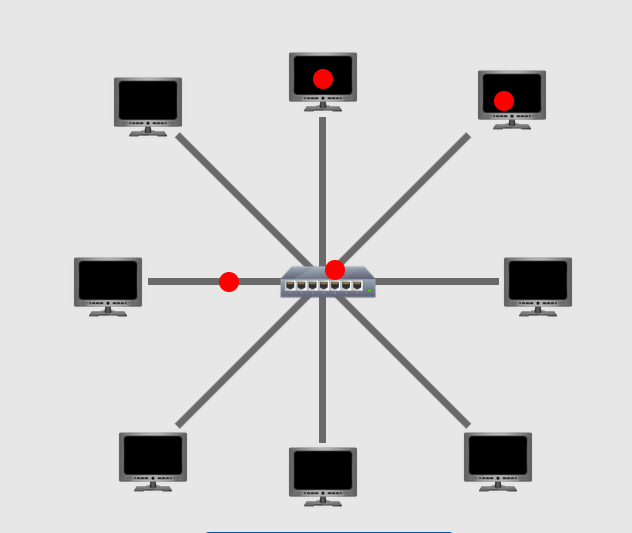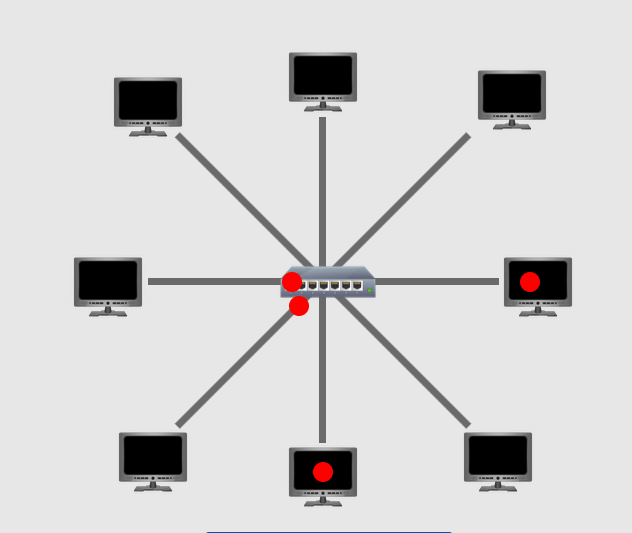
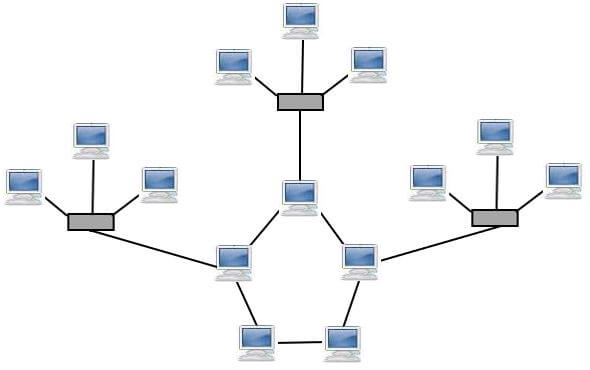
Tree Topology: Also called Hybrid Topology which is a combination of two or more topologies. For example, the below picture shows the combination of Ring and Start Topologies. This approach is basically customized to meet specific requirements and fault tolerance.
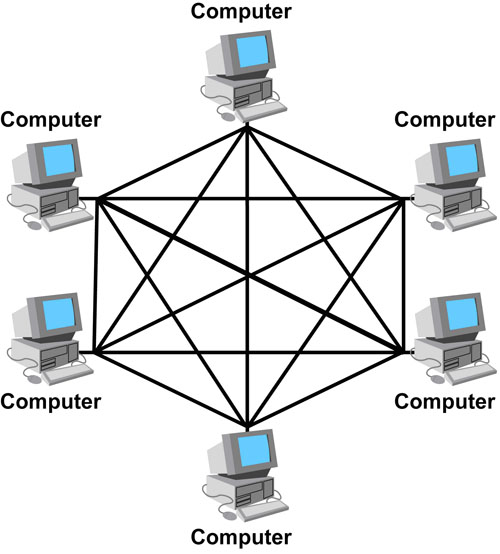
Mesh Topology: Every single device is connected to every single device in the network. Reduces data transfer time, but is expensive at the same time due to the use of more cable, and adding a new device into the network is also complicated and therefore less scalable.
Network Models
1. OSI (Open Systems Interconnection) Model
The OSI model is a seven-layer model that breaks down the communication process into seven distinct layers, with each layer responsible for a specific set of functions.
Application Layer: Provides services to end-users, such as email or web browsing.
Presentation Layer: Formats and presents data to the application layer.
Session Layer: Establishes, manages, and terminates sessions between devices.
Transport Layer: Provides reliable data transfer between endpoints.
Network Layer: Routes packets to their destination across multiple networks.
Data Link Layer: Transmits frames of data between devices on the same network.
Physical Layer: Transmits raw data bits over a communication channel.
2. TCP/IP Model
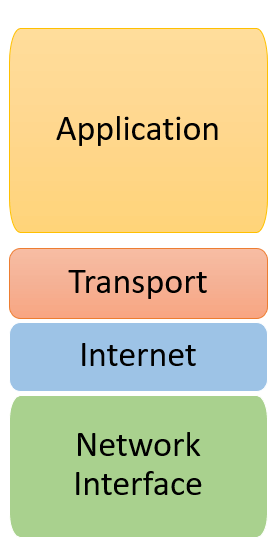
Application Layer: Provides services to end-users, such as email or web browsing.
Transport Layer: Provides reliable data transfer between endpoints.
Internet Layer: Routes packets to their destination across multiple networks.
Network Access Layer: Transmits data between devices on the same network.
There are some similarities and differences between these two models
Similarities:
Layered Approach: Both models use a layered approach to break down the complex process of network communication into smaller, more manageable components.
Common Functionality: Both models address similar functionality in terms of data transmission, addressing, routing, and error handling.
Compatibility: The TCP/IP model is often considered a practical implementation of the concepts defined in the OSI model. The TCP/IP model's network layer corresponds to the OSI model's network layer, and the TCP/IP model's transport layer corresponds to the OSI model's transport layer.
Differences:
Layer Structure: The OSI model has seven layers, while the TCP/IP model has four layers. The OSI model provides a more detailed and comprehensive breakdown of network functions, whereas the TCP/IP model combines some of the layers for simplicity.
Development: The OSI model was developed by the International Organization for Standardization (ISO) in the 1980s, whereas the TCP/IP model was developed by the Department of Defense (DoD) in the 1970s.
Flexibility: The OSI model is more flexible and allows for interoperability between different vendors' systems. The TCP/IP model is more commonly used in practice, especially on the Internet, and is considered more practical and efficient for real-world network implementations.
Network Security

Let's understand network security concepts such as Firewalls, IDS (Intrusion Detection Systems), IPS (Intrusion Prevention Systems), VPNs (Virtual Private Networks), and SSL (Secure Socket Layer).
Firewalls: Firewalls act as a protective barrier between a network and the outside world. They monitor and control incoming and outgoing network traffic, allowing authorized communication and blocking potentially harmful or unauthorized traffic.
IDS (Intrusion Detection Systems): IDSs are security tools that monitor network traffic for suspicious activity or patterns that may indicate a potential intrusion or attack. They generate alerts to notify administrators of any detected threats.
IPS (Intrusion Prevention Systems): IPSs are similar to IDSs but go a step further by actively blocking or preventing detected malicious activities. They can automatically take action to stop or mitigate attacks, such as blocking specific IP addresses or network traffic.
VPNs (Virtual Private Networks): VPNs create secure, encrypted connections over public networks like the Internet. They allow remote users to securely access a private network, such as a corporate network, by creating a virtual tunnel that encrypts data transmission.
SSL (Secure Socket Layer): SSL, now known as TLS (Transport Layer Security), is a security protocol that encrypts data transmission between a web browser and a web server. It ensures that data sent between the two endpoints is encrypted and protected from unauthorized access.
Network Troubleshooting

Network troubleshooting is the process of identifying and resolving problems that occur in a computer network. It involves resolving issues, finding their root causes, and implementing solutions to restore proper network functionality.
Some of the most common occurring issues are:
Network Congestion: Network congestion happens when there is too much traffic on a network, leading to slowdowns or performance issues. It can occur due to heavy data usage, insufficient bandwidth, or network bottlenecks. To troubleshoot congestion, you can identify the source of high traffic, optimize network resources, or upgrade network infrastructure if needed.
Packet Loss: Packet loss occurs when data packets sent over a network fail to reach their destination. It can be caused by network errors, faulty hardware, or network congestion. To troubleshoot packet loss, you can perform network tests, check for faulty cables or equipment, adjust network settings, or prioritize critical traffic.
Latency Issues: Latency refers to the delay experienced when transmitting data across a network. It can be caused by long physical distances, network congestion, or processing delays. Troubleshooting latency involves measuring and analyzing network delays, optimizing network settings, and minimizing unnecessary network hops.
Checksum:
A checksum is like a digital fingerprint that helps detect errors in data. It's a calculated value based on the data, and it's sent along with the data. When the data is received, the recipient calculates a new checksum and compares it with the received checksum to see if the data arrived without errors.
Three-Way Handshake:
The three-way handshake is a process that two devices use to start a connection. First, one device sends a message to the other saying "let's connect." Then, the other device responds with a message saying "I got your message, let's connect." Finally, the first device confirms the connection by sending another message. This handshake ensures both devices are ready to communicate before they start sending data.
Control Plane:
The control plane is like the brain of a network. It handles the management and coordination of network devices. It includes protocols and mechanisms that help devices exchange information, make decisions, and configure the network. The control plane is responsible for tasks like routing, network discovery, and network policy enforcement.
MiddleBoxes:
Middleboxes are network devices that sit in the middle of data transmission paths. They perform various functions to manage and secure network traffic. Examples of middleboxes include firewalls, load balancers, and intrusion detection systems (IDS). These devices help control and direct network traffic, ensure security, and optimize network performance. They play a crucial role in filtering, inspecting, and modifying network traffic as it flows through the network.
Timers:
Timers are like alarms used by networking protocols to keep track of time. They help protocols perform specific actions or trigger events after a certain duration or when a condition is met. For example, timers can be used to resend data if it's not acknowledged within a set time or to control the timing of certain protocol operations. They ensure that network protocols function correctly and efficiently.
Cookies:
Cookies are small text files stored on a user's device by websites they visit. They help websites remember user preferences and store information, such as login credentials or items added to a shopping cart. Cookies enhance the user experience by allowing websites to personalize content and provide targeted advertisements based on browsing behavior. They are harmless text files and can be managed or cleared by the user.
Error Status Codes:
Error status codes are numbers returned by web servers to indicate the status of a requested web page or resource. The codes are grouped into categories, such as 2xx for successful responses, 4xx for client errors, and 5xx for server errors. Common examples include 404 (Not Found), indicating that the requested page does not exist, and 500 (Internal Server Error), indicating an issue with the server. These codes help diagnose and troubleshoot issues when browsing the internet.
Some essential commands to know:
Ping is a command that is used to test the connectivity between two devices. It sends ICMP echo requests to the target device and waits for ICMP echo replies. If the target device replies, it means that the connection is working.
ping google.comTraceroute is a command that is used to find the path taken by the packets to reach the target device. It sends ICMP echo requests to the target device and waits for ICMP time-exceeded messages. If the target device replies, it means that the connection is working.
traceroute google.comNslookup is a command that is used to find the IP address of a domain name. It sends a DNS query to the DNS server and waits for a response.
nslookup google.comNetstat is a command that is used to display the network connections and routing tables. It can be used to find the open ports on a device.
netstat -tulpnHostname is a command that is used to display the name of the current host.
hostname
In this blog, we have explored various essential concepts in computer networking, ranging from network models and protocols to network security and troubleshooting. By gaining knowledge in these networking topics, you now have a solid foundation to understand how networks function, how data is transmitted, and how to address potential issues. As technology continues to evolve, networking will remain a crucial aspect of our interconnected world.

Thank you for reading this blog till the end! I hope you found it informative and helpful in gaining a better understanding of computer networks, if yes then please leave a like on this. I appreciate your support and interest in my content. If you have any specific topics or questions you would like me to cover, please let me know.